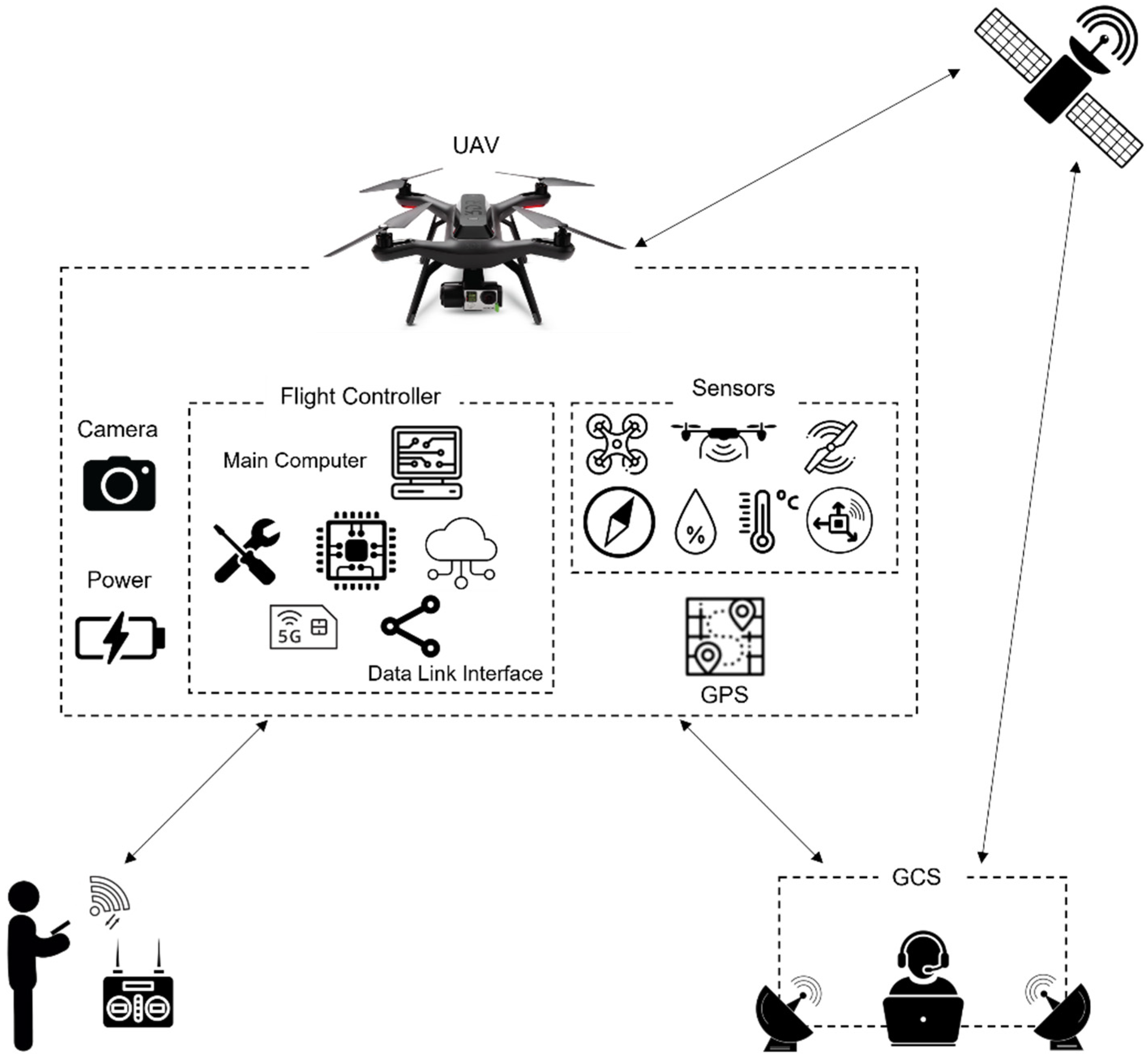
Applied Sciences | Free Full-Text | Drone and Controller Detection and Localization: Trends and Challenges
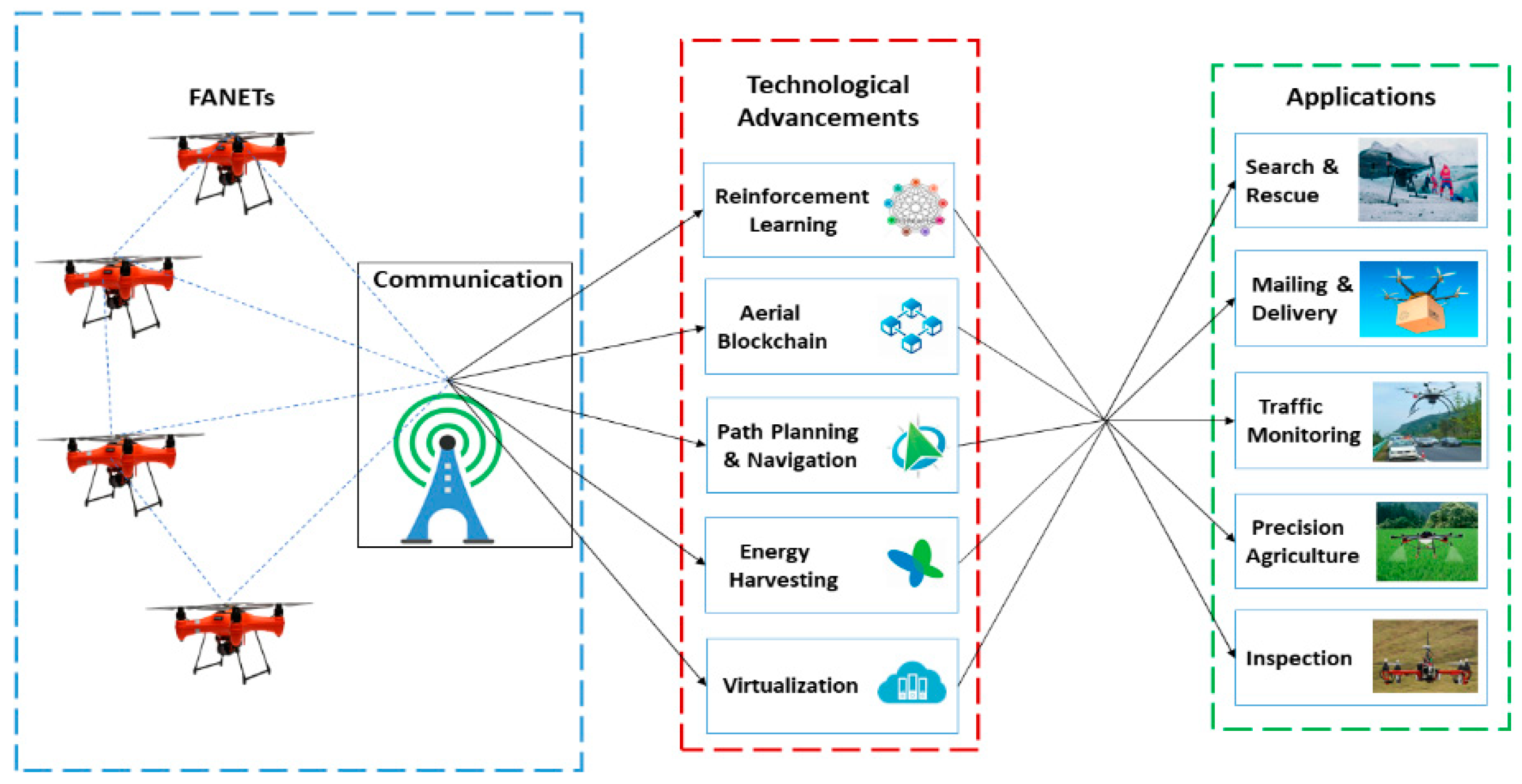
Drones | Free Full-Text | A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics

Tech Times | Companies try hijacking and shooting drones - To keep flying objects out of high-risk areas | News | Jamaica Gleaner